Technology Tips: September 2015 Edition

|
Skyward IT Services Network Infrastructure and Security Specialists |

Dusty Laptop?
If you've owned your laptop for more than a year, chances are good that the inside is not as clean as it used to be. Dust particles clog your laptop's fans, vents, and heat sinks, preventing it from cooling down properly. As a result, your fan may need to run at full speed, draining your battery life. In extreme cases, this dust may also throttle the CPU, causing noticeable performance issues. Laptops are not designed to be opened up, but it is possible to remove most of the dust without a degree in computer engineering. Using a can of compressed air, spray the inside of your laptop's vents. To prevent damage to the fan, always use short bursts instead of one continuous blast. Note: Compressed air should not be used on a running computer due to the potential fire hazard. Once you've performed this simple procedure, your fan should be quieter and run less often.
Once you're finished, if the fan is still loud and you are comfortable with computer repair, you may try disassembling the laptop to remove dust from areas that are otherwise inaccessible (don't be afraid to ask an IT professional for help). Check to see if your laptop is still under warranty. Oftentimes, you can send it back to the manufacturer for cleaning to minimize the risk involved.
MS Office Screenshot
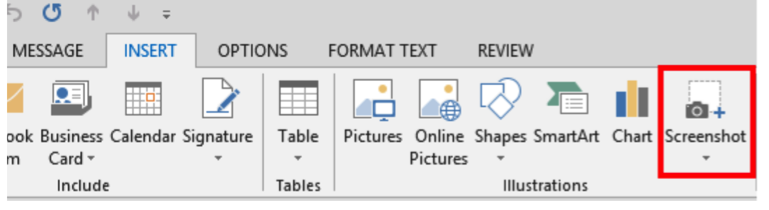
Tired of using third-party software for taking screenshots? Or saving them to your desktop then copying the files into your documents? With MS Office, you can use the built-in screenshot application to add photos to MS Office documents right from the Office product you are using.The screenshot button is located in the Insert tab on the top ribbon of most MS Office products. Just click the drop-down arrow and select an active window or screen clipping to choose what you’d like to capture.
Mastering this technique will enable you to streamline the process of creating documentation, tutorials, or trying to explain something over an email.
Safe Computer Disposal
More often than not, when someone wants to get rid of an old computer, they take it to a computer recycling facility and never think twice about the hard drive. As identity theft and data hacking schemes become more complex, it's more important than ever to make sure your information can't be recovered from that old computer. So, what can you do to prevent people from resurrecting your personal information?Option 1: Wipe the drive
The simplest way to protect your info is to download a drive wiper. These programs completely overwrite the hard disk with useless data, rendering any previous data on the drive unsalvageable. The U.S. Department of Defense recommends three full wipes: once with zeroes, once with ones, and then once with a random character. Unless you have information that could pose a threat to national security on your hard drive, one wipe should suffice.
If you're using an internal drive, try using the CD-based program CBL Data Shredder*. It comes as an image file that you burn to a CD/DVD. When you restart your computer, you boot from the CD/DVD instead of your hard drive. Make sure you don't have anything left to do - you can't use your computer while wiping with this method.
For external drives, use Disk Wipe*. It's a small Windows program that can be launched on demand - and you can use your computer while you wipe for those last-minute tasks.
Both methods take about 2 and a half hours for a 250 GB drive.
* Note – Skyward does not endorse any particular brand or product over another; these are just two that we know can get the job done.
Option 2: Smash
The second option is a lot faster (and probably more satisfying), but you’re going to get your hands dirty. Start by disassembling your computer and removing the hard drive. Next, open the case of the hard drive until you expose the metal magnetic disk inside. Take a drill or a hammer and start inflicting damage on the magnetic drive platter (it may break into pieces, so be sure to wear eye protection). The more you smash, the harder it will be for someone to put it back together. Plus, who doesn't like to break things every once in a while?
Malware of the Month – Browser Toolbars
Browser toolbars have been around for years. In the past couple of months, however, they have become an overwhelming mess due to their attachment to some popular, free software programs. Toolbars are not only irritating, they can also take liberties with your privacy and browsing experience.Here are just some of the things toolbars can do to you:
- Change your homepage and default search engine without permission or awareness.
- Track your browsing activities and searches.
- Display annoying ads and manipulate search results.
- Take up a significant amount of vertical space inside the browser.
- Slow down your browser and degrade your surfing experience.
- Battle each other to the point that "normal" add-on handling becomes unmanageable.
- Make themselves all but impossible to fully uninstall.
To reduce your chance of acquiring these unwanted "free gifts," always pay close attention when installing new software. A software installer often includes optional installs, of which a toolbar may be one. Always opt for the custom installation, deselecting anything that is not familiar, especially optional software that you never wanted to download in the first place. It goes without saying that you should never install software that you don’t trust.
If you do find an unwelcome addition, a good first step for removal is checking the installed programs on your computer to see if you have a choice to uninstall it. You may also need to run a malware removal tool, such as Malwarebytes, to fully clean your computer.
Bonus – Live Threat Updates
For a fascinating look at the Internet attacks that are happening around the world right now, check out the Norse IPViking Live Attack Map.Need help securing and optimizing your network? Check out the many IT Services we have available and contact us today.
Thinking about edtech for your district? We'd love to help. Visit skyward.com/get-started to learn more.
|
Skyward IT Services Network Infrastructure and Security Specialists |

 Get started
Get started