Technology Tips: August 2018 Edition

|
Skyward IT Services Network Infrastructure and Security Specialists |
Screens got the blues?
Blue light, also known as high-energy visible (HEV), makes up 1/3 of all visible light. It’s everywhere—it’s what makes the sky look blue. It increases alertness, improves memory, and elevates our mood. In fact, light therapy for seasonal affective disorder uses HEV light.However, our eyes are not very good at blocking HEV light. Blue light can penetrate to the very back of our eyes, putting us at risk for macular degeneration, which can lead to permanent vision loss. Eye care providers are concerned about the extra HEV light exposure humans are getting from digital devices. People who have had cataract surgery are especially at risk.
Here’s how to protect your eyes from excessive blue light exposure:
1. Adjust your settings: On both desktop and mobile devices, you’ll probably find blue light adjustments in the display settings. Here are some options for iOS, MacOS, Windows 10, and Android.
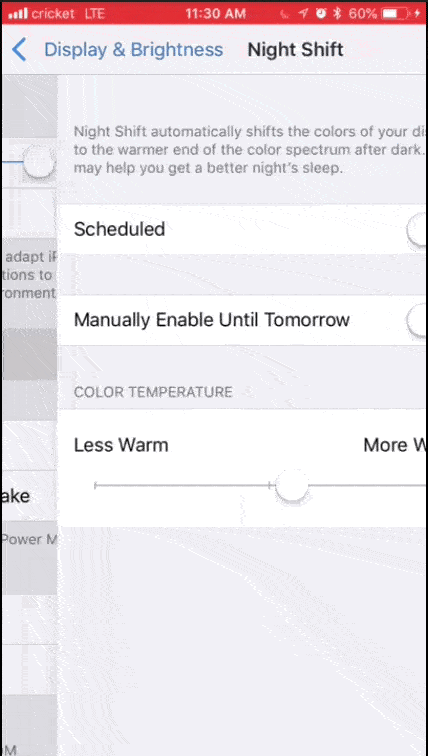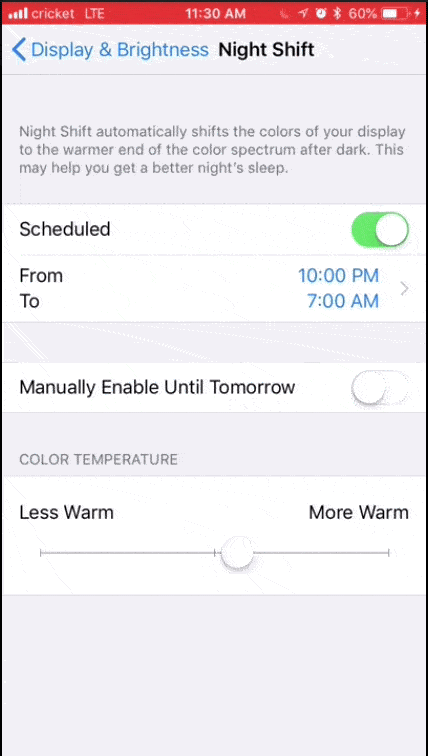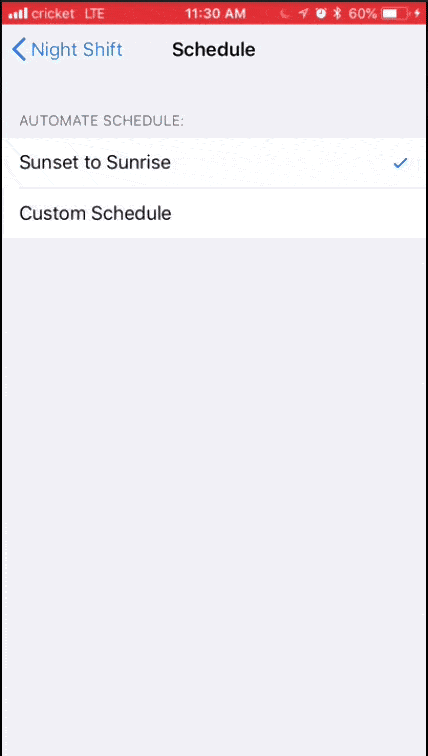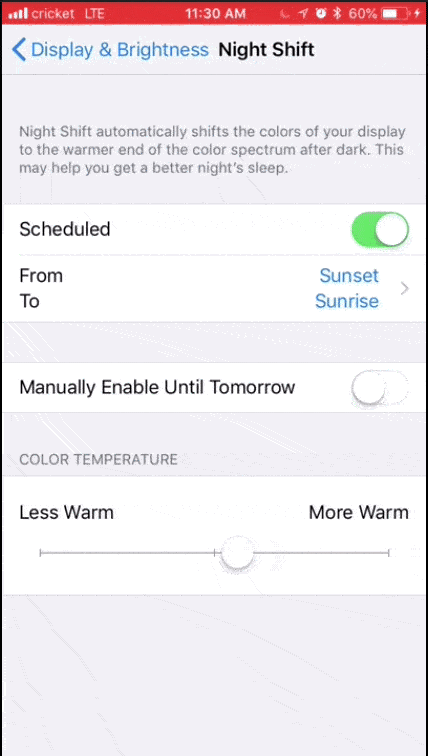
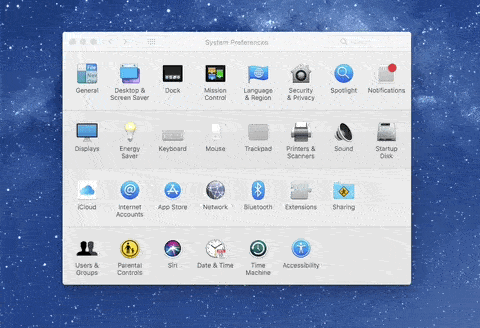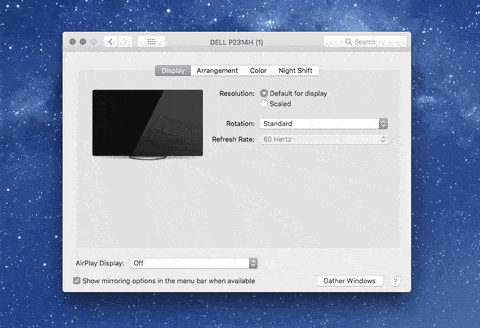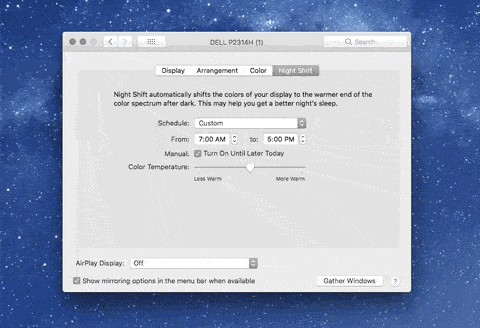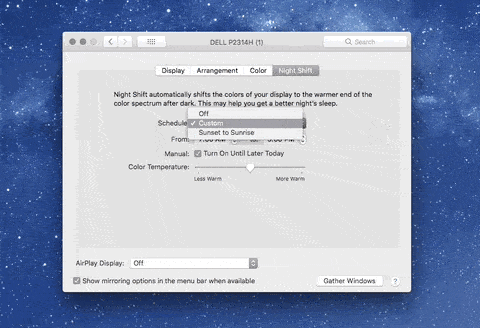
MacOS night shift
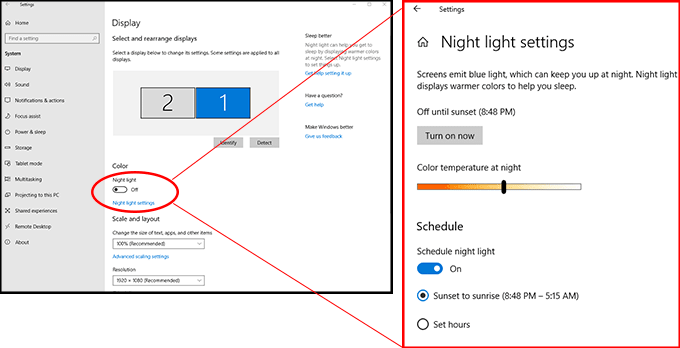

2. Try an app: There are several apps available for Android and iOS. Some have built-in timers so you don’t have to remember to adjust settings manually.
3. Use protective eyewear: Ask your optometrist or optician if they have recommendations for lenses designed to filter excess blue light. These lenses may be tinted yellow to balance the blue light.
Global citizenship goes digital
With so many tools available to connect people around the world, teachers are eager to share with students, but safe and welcoming environments are crucial. Here are three options from reputable global education sources to connect classrooms without increasing risk.UNICEF Voices of Youth: A global community of bloggers founded in 1995, Voices of Youth gives students a place to learn more about global issues from students like themselves and add their own perspective, too.
Microsoft Skype in the Classroom: Lessons, guest speakers, virtual field trips, and more await educators looking to expand the boundaries of their classrooms. Mystery Skype, a particularly interesting component, brings classes together from different parts of the world. Students must ask yes or no questions of their mystery classmates in order to figure out where they are from.
PenPal Schools: Students are matched with a partner from somewhere else in the world on projects chosen by their teachers. Partners are chosen based on age, gender, and location to respect cultural norms. Certain topics of study are free, and others require a premium package. Either way, PenPal Schools has committed to keeping student data safe as they forge global connections.
Web refresh
Unlike books and periodicals with their convenient copyright page, websites often don’t provide their readers the courtesy of knowing when their content was published. You can see when a web page was last modified using these methods.For beginners and non-coders: Visit the Internet Archive and enter the URL of the page you’d like to check. This method will give you a basic idea, but not always an exact timestamp, of the last time the page was updated.
For intermediate Internet veterans: Visit the page you’d like to check, then type javascript:alert(document.lastModified) into the address bar. Note that if you paste the string into the address bar, many sites will remove the “javascript:” signifier for security reasons, and you may have to type it in manually. Hit enter and you should see a dialogue box with the date and time pop up. If the site runs on dynamic scripts, it will display the current date and time because the site is constantly updating itself.
Malware of the month
New malware is emerging courtesy of North Korean hackers known as Hidden Cobra or Lazarus Group. Named Typeframe, the malware consists of 11 different pieces of Windows .exe files and even a Word document. The malware files are able to download and install additional malicious files in order to connect to control centers for further commands.The same group is thought to be responsible for the WannaCry ransomware. Typeframe is the 12th version of malicious computer file believed to have been created by Hidden Cobra, which also creates tools for mounting distributed denial-of-service (DDoS) attacks.
Follow-Up Resource: IT Services
Need help securing and optimizing your network? Check out the many IT Services we have available and contact us today.Thinking about edtech for your district? We'd love to help. Visit skyward.com/get-started to learn more.
|
Skyward IT Services Network Infrastructure and Security Specialists |

 Get started
Get started