Technology Tips: January 2026 Edition

|
Skyward IT Services Network Infrastructure and Security Specialists |
Pretexting attacks
If you’ve ever wondered how hackers find specific details about your life, you probably don’t have to look farther than social media. Bad actors often use pretexting to target and hook victims.Pretexting is when cybercriminals use a made-up story, or pretext, to convince their target to do something that will harm themselves or their organization. Hackers will look for posts online such as:
- “Thank you to our COO Millie James for donating to Toys for Tots.”
- “I’m heading on a trip to the Bahamas with my son James. See you in two weeks!”
- “My wife Laura and I just bought a house! We are loving the Pinewood Neighborhood!”
These examples share names and personal details of each individual that a hacker could use to manipulate their victims.
To mitigate these types of attacks, avoid sharing personal details online. Verify all requests to connect or be your social media “friend.” Confirm your social media privacy settings. Be cautious if someone is texting you and then wants to move the communication to social media or WhatsApp—these are telltale tactics of a hacker.
Delay Office Outlook emails after hitting send
If you haven’t sent an email to the wrong person or forgot an attachment, you just haven’t been in corporate America long enough. Office Outlook gives you the option to delay your emails by 5, 10, 15, 20, 30, 60, or 120 seconds after hitting send.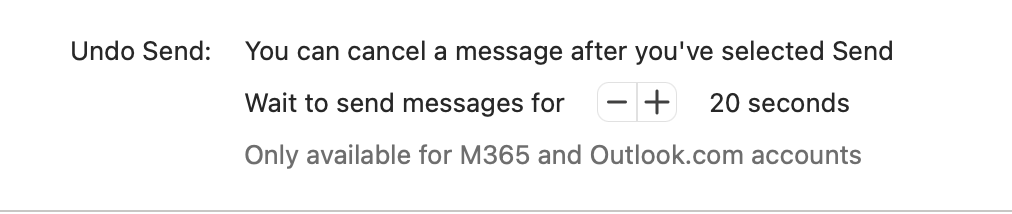
Go to Outlook > Settings > Composing > Undo Send > then select your preferred time frame. In just a few clicks you’ll be set up for a delayed send and peace of mind.
The pros and cons of contactless payments
The use of contactless payments is rising, and for many convenient reasons. As with all new technology, you may be wondering what the risks are.The pros:
- Time savings: Contactless means that you aren’t handling cash or waiting for change, and it also keeps lines going a bit quicker.
- Flexibility: You can have your cards digitally saved to your phone, so you no longer need a bulky wallet.
- Health: Not having to handle cash or touch a card reader is a perk for those with health concerns.
The cons:
- Limits: Not all retailers accept contactless payments, so it’s important to have a backup option when shopping.
- Safety concerns: A PIN is not used in these transactions, so there isn’t a way for cashiers to determine if the device being used is stolen.
- Technical: A contactless payment option is not for consumers that may face technical barriers, such as technical knowledge or not having a compliant smart phone.
Malware of the month
A new Comparitech study shows that U.S. companies take an average of 4.1 months to report a data breach after a ransomware attack, with reporting times rising from 2.1 months in 2018 to over five months in 2023. Some sectors take even longer—law firms average 6.4 months, and one healthcare breach went unreported for 38 months.This delay leaves victims unaware that their sensitive data may already be circulating on dark web leak sites, sometimes posted by attackers within one month if ransom negotiations fail. To keep yourself safe, always assume delays in breach notifications and proactively protect your data by using strong passwords, monitoring financial accounts, enabling MFA (multi-factor authentication), and staying alert to identity theft risks.
Thinking about edtech for your district? We'd love to help. Visit skyward.com/get-started to learn more.
|
Skyward IT Services Network Infrastructure and Security Specialists |

 Get started
Get started