Technology Tips: April 2025 Edition

|
Skyward IT Services Network Infrastructure and Security Specialists |
The scams start coming and they don't stop coming.
Have you noticed? Smishing attempts have been ruthless lately. Keep on the lookout for texts with an urgent or threatening tone, like this one about paying fake toll fees. Notice how this text also includes a link – clicking on it (or copy & pasting) could lead to malware. When in doubt, visit the state websites of places you’ve visited lately to see if you owe any fees.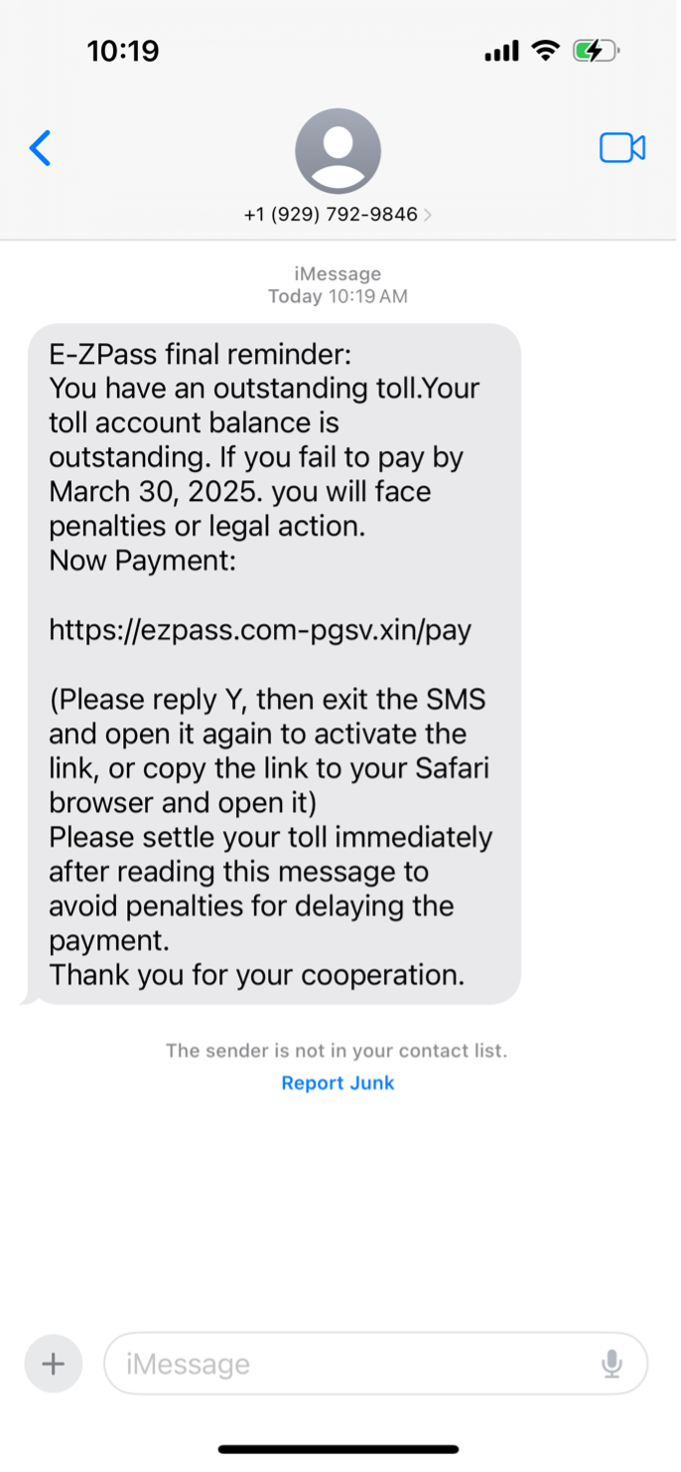
Safari’s intelligent tracking prevention
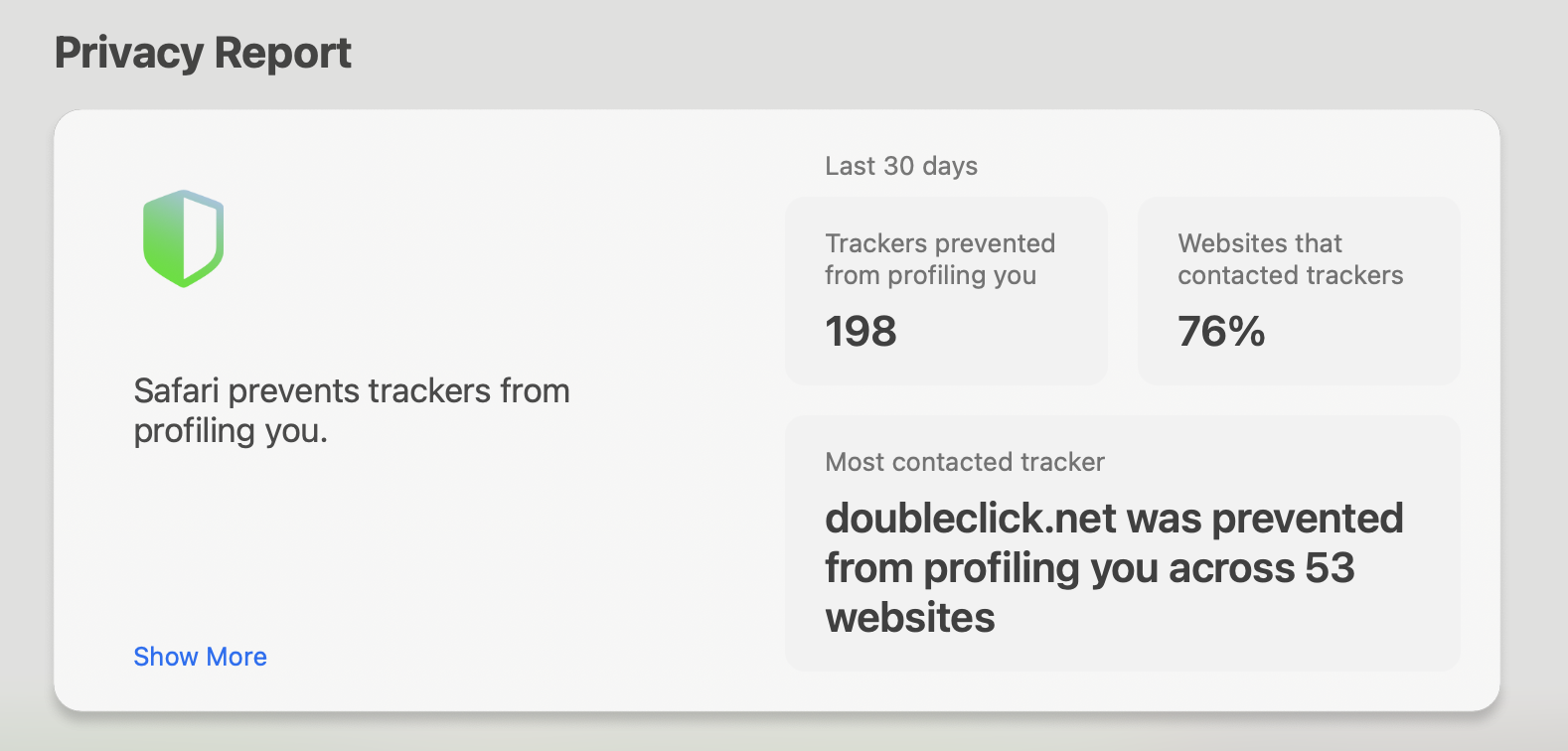
If you use Safari, you may have noticed this Privacy Report feature. It feels a bit jarring, but it is helpful to know that there are browsers actively working for your best interest.Intelligent Tracking Prevention (ITP) limits cross-site tracking and cookies (think of ads popping up after you visit an online store). While marketers may hate this feature, it keeps your browsing history private. This could mean more money in your wallet by deterring those highly specific ads.
Brush up on your mobile malware knowledge
While hackers are still targeting corporations and businesses, they are preying on individuals now more than ever. Many people are continuing to work from home using their own personal devices, which can be a big security threat. Here’s how bad actors exploit mobile and personal devices: Remote Access Tools (RATs): RATs can steal a lot of data. When a device gets infected, hackers can access call history, web browsing history, and GPS coordinates. They can also enable the device’s camera and send SMS messages.
Advertising click fraud: This form of malware allows a hacker to generate ad revenue through fake clicks.
Polymorphic malware: When it infects a file, part of the malware mutates to make it difficult to detect (yikes!). This unfortunately makes antivirus scans unreliable.
Keyloggers: Like the name suggests, this type of malware records your keystrokes to capture important passwords and login credentials.
Jailbreaking and rooting: If you root an Android device or jailbreak an Apple device, it loses all manufacturer security protections.
Malware of the month
Wanted by the FBI: Cyber espionage group Aquatic Panda
China-linked group Aquatic Panda, who are employees of Chinese tech company i-Soon, has been causing mayhem for years. They’ve been charged with computer and wire fraud among governments, religious charities, and think tanks across the United States, France, Türkiye, Thailand, Hungary, and Taiwan. Their actions took place during January–October of 2022 and officials are now finding evidence.
The Diplomatic Security Service’s Rewards for Justice Program is offering up to $10 million for information.
Thinking about edtech for your district? We'd love to help. Visit skyward.com/get-started to learn more.
|
Skyward IT Services Network Infrastructure and Security Specialists |

 Get started
Get started





