Technology Tips: February 2024 Edition

|
Skyward IT Services Network Infrastructure and Security Specialists |
Is your tech true love or due for a trade-up?
Hate to be the bearer of bad news this season of love, but some tech breakups are waiting to happen. We can’t decide for you, but here are a few ways you might deserve better.Passwords: Post-its or Password managers?
Keeping your passwords close requires a secure strategy, and writing down passwords on post-it notes is not a great strategy. Instead, upgrade to a reputable password manager and rest easy knowing it’s got your back—and a stock of complex passwords you’ll never have to think about.Smart homes vs. offline appliances?
Does anyone really NEED a coffeemaker or dishwasher that’s Wi-Fi capable? We’ll let you decide, but consider: anything connected to your network could provide an access point for a bad actor. You’re worth protecting. And no one needs a smart toothbrush.Patch managers vs. update avoidance
It’s easy to click “ask later” as a user who doesn’t understand the importance of updates. Maybe this is the year you treat yourself and your network to a new patch manager strategy. No more begging avoidant users to update machines, software, or settings!Phishing drills vs. phishing scares
This one has got to be a no-brainer. You deserve better than the same old malicious email runaround! Get your training program updated and send out a few phishing drills from time to time—the data you catch will be eye-opening.Caution with get to know me trends online
If you’re a reader of a certain age you may recall the text-based, chain-letter style ancestors of today’s “get to know me” social media challenges. But did you know these can be wielded as password-guessing tools? Think about the types of security questions your bank and other organizations require. These are designed to be trivia about your life (think your first-grade teacher’s name or your first pet). Be suspicious of challenges designed to get to know you that mask innocuous questions that might fill a portfolio of personal information a bad actor can use to impersonate you—and gain access to your accounts.Plus, nowadays social networks even encourage everyone to reply to the same challenge template with photos, notes, responses, and more. Are you sure you know who created this template? Where is your data being stored, and by whom?
This caution is powerful, not just for us, but for the little digital citizens in our lives as well. There’s a lot of trust placed in social media (Gen Z considers this digital world to be particularly friendly) that’s easily exploited.
Phishing during awards season
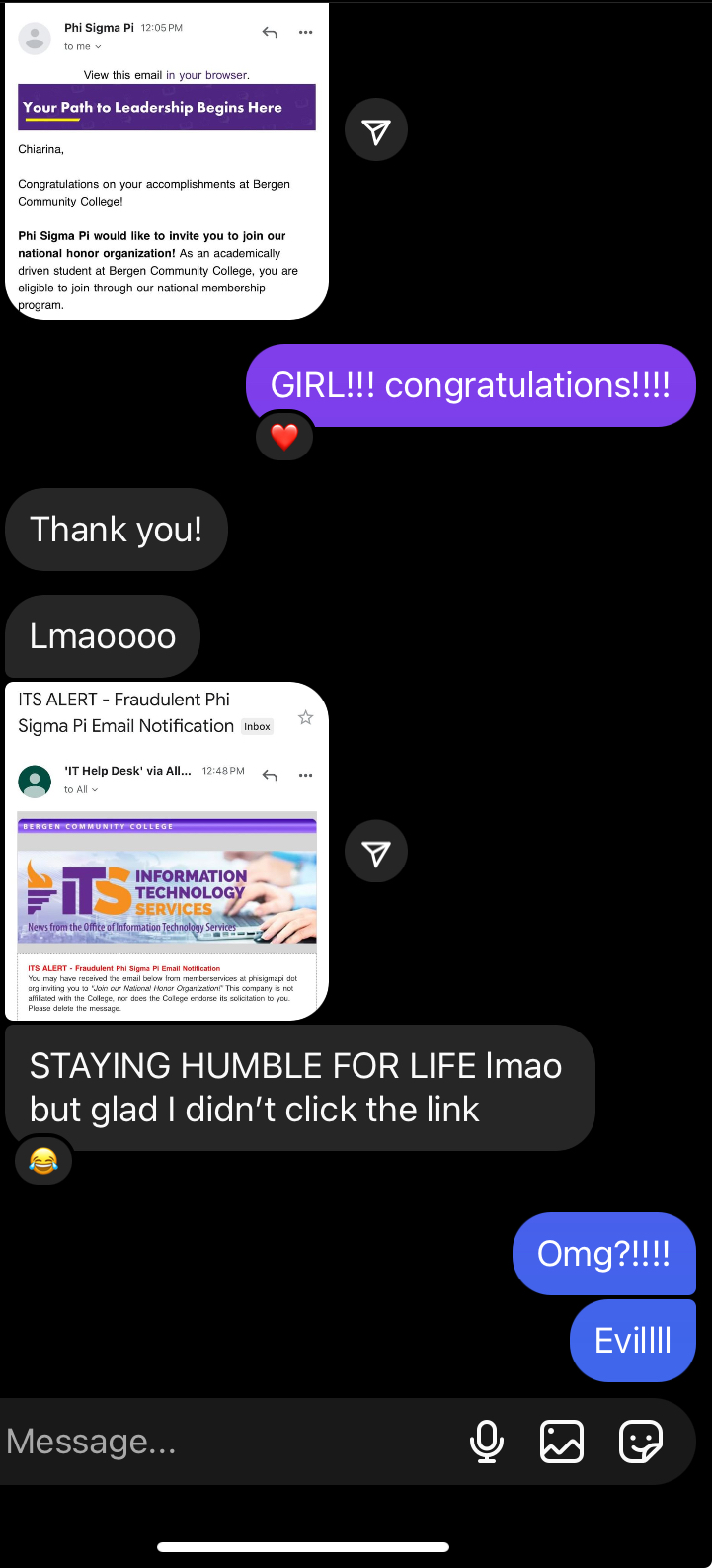
Often we describe phishing emails as using a sense of urgency to spur a quick reaction. One tricky technique relies on threats, but bad actors are equally capable of using good news to inspire clicks that capture credentials and more.Take this real-life example from a student who received flattering news about her invitation to an honors society, only to receive an update from the IT staff warning folks it was, in fact, too good to be true. “Stay humble for life,” was the student’s wise reaction (and there’s no doubt she’ll go on to achieve great things).
Malware of the month
We think of biometric data such as facial recognition as a super security strategy. Guess it’s no surprise threat actors agree such data is valuable to their cause. A recent discovery of a rare iOS Trojan is capable of capturing facial recognition data from iOS devices. Read more about how it was discovered and what it means for device security going forward.Just for fun
Thinking about edtech for your district? We'd love to help. Visit skyward.com/get-started to learn more.
|
Skyward IT Services Network Infrastructure and Security Specialists |

 Get started
Get started





