“Leave them to their own devices” may be a punny security strategy, but any edtech leader knows that getting proactive is the only way to turn perpetually at-risk staff into a knowledgeable first line of defense.
The best way to protect your data (and that of your students) is to educate potential targets about the threats they face in the virtual world. Three of these threats in particular have risen to the top of many district to-do lists.
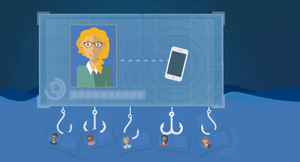
1) Phishing
Phishing is what it sounds like: scammers use bait, often in the form of an official-looking email, to get the recipient to enter personal information or click on sites infected with malware. The most effective of these are almost indistinguishable from the real thing, and just one click can lead to disaster.An uptick in phishing attacks has led to the launch and success of tools like KnowBe4, which – among other services – offers a platform for tech leaders to do a little faux phishing of their own. District employees receive mock phishing emails, and when someone clicks on a link, they are directed to a page that explains the dangers of phishing (with optional training videos or in-house follow-up). CTOs now have the data they need to assess the percentage of users who are “phish-prone” and follow up accordingly.
Pro tip: One edtech leader we spoke to stressed the importance of positioning this as a critical security drill, rather than a “gotcha” opportunity. After using KnowBe4’s tools, he saw open rates plummet from 40% to 13% to 11% after just three sends. As staff learned to identify the signs, it became a competition to see who could spot the phishing emails and avoid getting duped, which is both fun and beneficial for the district.
2) Google Drive Tools
Many schools are Google shops these days, but in some cases, implementation has outpaced training. The flexible sharing options available in Sheets, Docs, or Slides can make it easy to unintentionally share a sensitive file with another person, or worse – anyone on the Internet.Administrators could limit sharing options for your entire domain in the Google Apps Control panel, but that drastic action can be a detriment to usability. Training and coaching are almost always better options. The owner of the document controls the level of access granted to individual collaborators: can view (can view or print files), can comment (can make comments or suggestions), or can edit (can make changes to the file). Sharing settings can be updated at any time, so it doesn’t hurt to err on the side of caution.
Link sharing is an easy way to widely distribute instructions, polls, and other public information. If you don’t anticipate sharing a document extensively – or if it contains any sensitive information – it’s safest turn off link sharing. If you do use link sharing, carefully decide whether anyone with the link can view, can comment, or can edit the document being shared.
Pro tips: Only share with the people who need the document, and only for as long as they need it. Double check that any public link is free of personally identifiable information. Organize shared documents in folders that are easy to access and review.
3) Local data storage
What happens when data is exported from a student information system or a learning management system? It’s the district’s responsibility to limit access to student information to those with a legitimate educational interest, but when a staff member downloads rosters or grade sheets to a computer, all of the programmatic security safeguards that were protecting that data in the system are null and void.This is one of the tougher threats to counter, because so much of it is the responsibility of the individual teacher or support person. Initial education and persistent reminders are key here. Exports should be limited to only the most necessary fields, and sensitive folders should be password-protected whenever possible (with no passwords written on sticky notes on the computer monitor). If every employee is trained to delete items the moment they don’t need them anymore and empty the trash with every sensitive deletion, that’s one more physical security threat diminished.
Pro tip: Try a multimedia approach to training that includes short, easily accessible screen capture videos for any of the relevant steps. Examples include password-protecting a folder, removing fields from an export, and sorting files by date to help identify candidates for deletion.
You wouldn’t assume your staff knows the fire escape route or tornado safety plan without executing some practice drills – don’t make that mistake when it comes to information safety and security. When you get proactive about security, you’ll be protecting more than just your network. Your staff, students, and community will all be safer because of your efforts.
How much access is too much access? Brush up on privacy and security basics with Too Much Access: The FERPA Compliance Gap.
WHAT'S NEXT FOR YOUR EDTECH? The right combo of tools & support retains staff and serves students better. We'd love to help. Visit skyward.com/get-started to learn more.

|
Casey Thompson Locking Down Student Data |